

The Company stipulated "Operating control of information and communications security inspection" in 2009. In order to increase the internet security, establish appropriate management construction, effectively distribute the responsible of information systems security, implement the information systems security in promotion, and Coordinate the implementation of various information security measures to ensure the level of protection of the information security system.

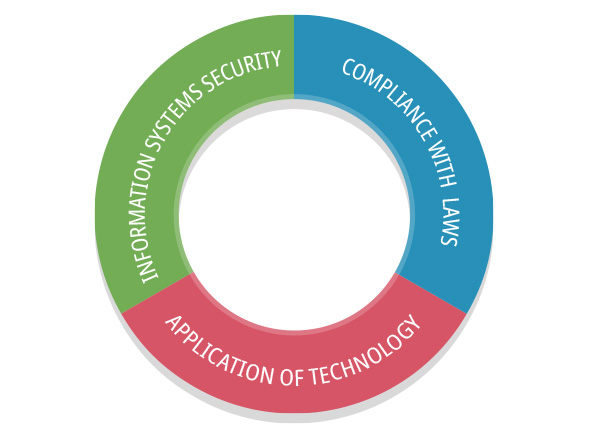

| Information systems security tactics | ||
|---|---|---|
| Information systems security | Improved on management system Controlling risks and strengthening prevention Build a defense system |
Improved on management system continuously, include strengthening the educational training, Establishing information systems security risk management construction, and furthering protection technology. |
| Compliance with laws | Regular inspection / revise Establish compliant circulate mechanisms |
Establish compliant circulate mechanisms. Review and revise internal operating standards regularly to comply with international security standards and laws in overseas regions. |
| Application of technology | Internal and external data collection Anticipate threats and decisions |
Check on each Dept. for the security monitor regularly. Predict information security risks, and make countermeasures earlier. |

On August 2017, the customer center received notification from players that couldn't enter into the game successfully. Members of IT and development checked on the company's intranet and found that the connection is stable. Further detection of suspicious external attacks that seized by hackers and asked for ransom. The company launched related contingency measures immediately. During 24hrs to offensive and defensive by relevant members, the hacker knew there were no breach then retreated on the next day. This was an DDoS (Distributed Denial-of-Service) attack event which affected players playing games. The company is implementing improved measures for three major aspects, strengthening the test of information systems security management, monitoring and managing mechanisms, adjusting basic environment construction.


